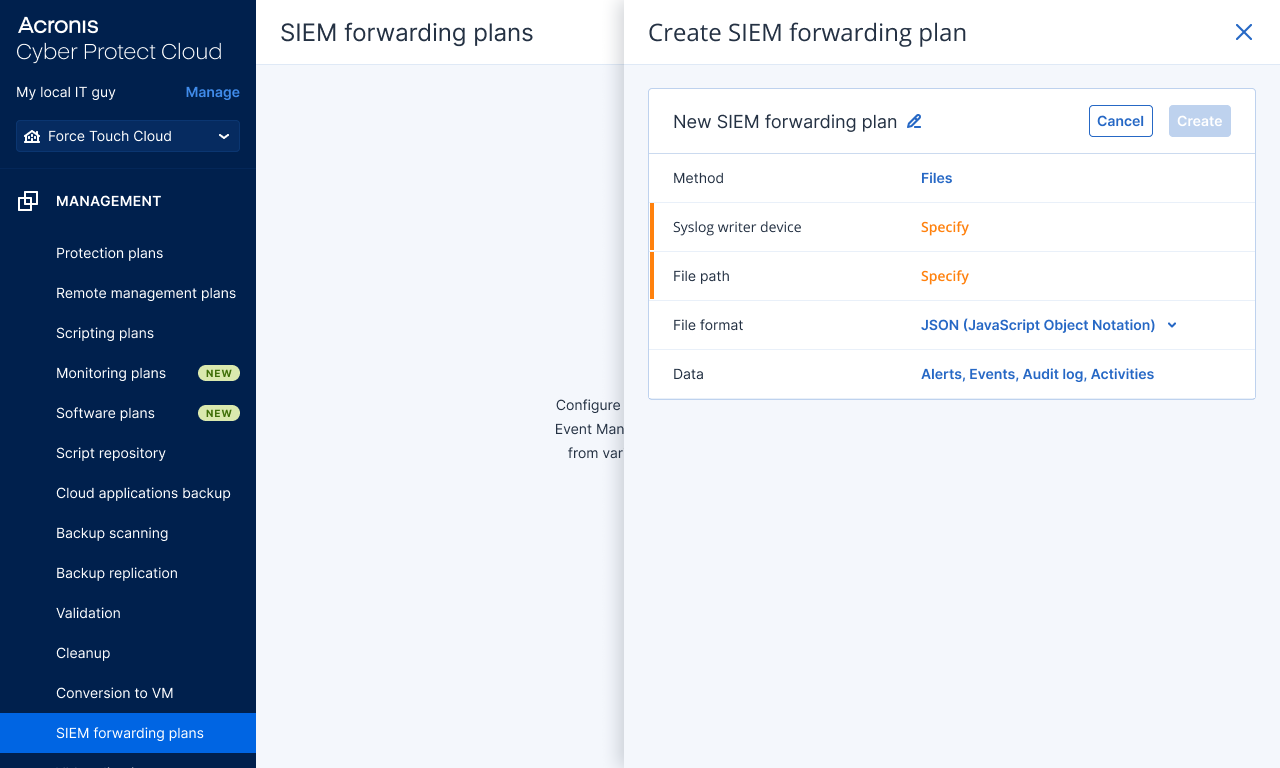
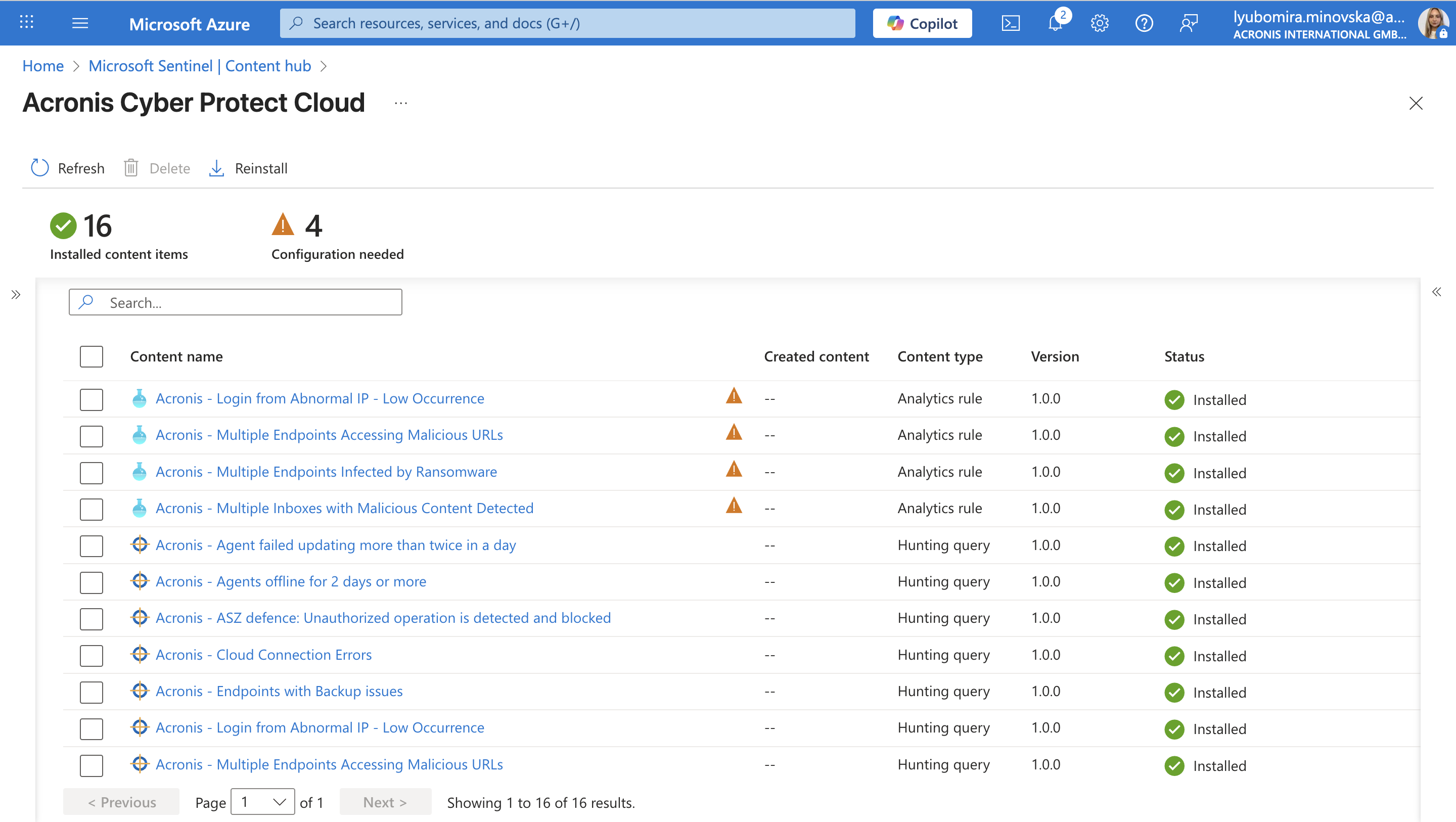
Simplify security posture by integrating Acronis Cyber Protect Cloud with Microsoft Sentinel.
Now with Microsoft Sentinel integration, MSPs will gain full visibility into customers networks and will be able to search for threats across all managed workloads, and correlate events from both security and data protection applications, and run response actions based on collected telemetry, that is now enriched with Acronis data. The integration includes 12 custom hunting queries and 4 detection rules which are uploaded directly into the Microsoft Sentinel Content library.