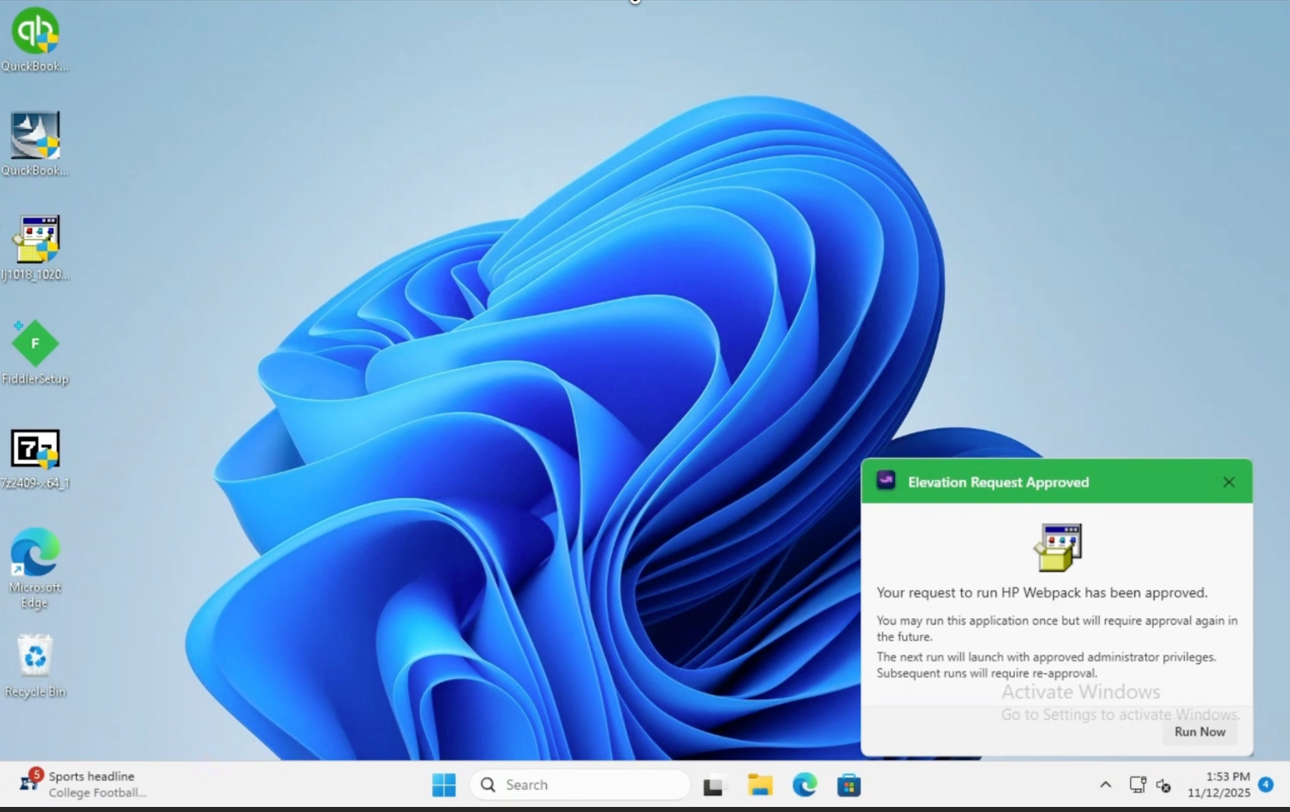
End User Elevation in Action
Control and enforce least privilege with the platform designed to work the way MSPs do.
Seamlessly deploy utilizing pre-built scripts for Acronis RMM and enable your technicians to:
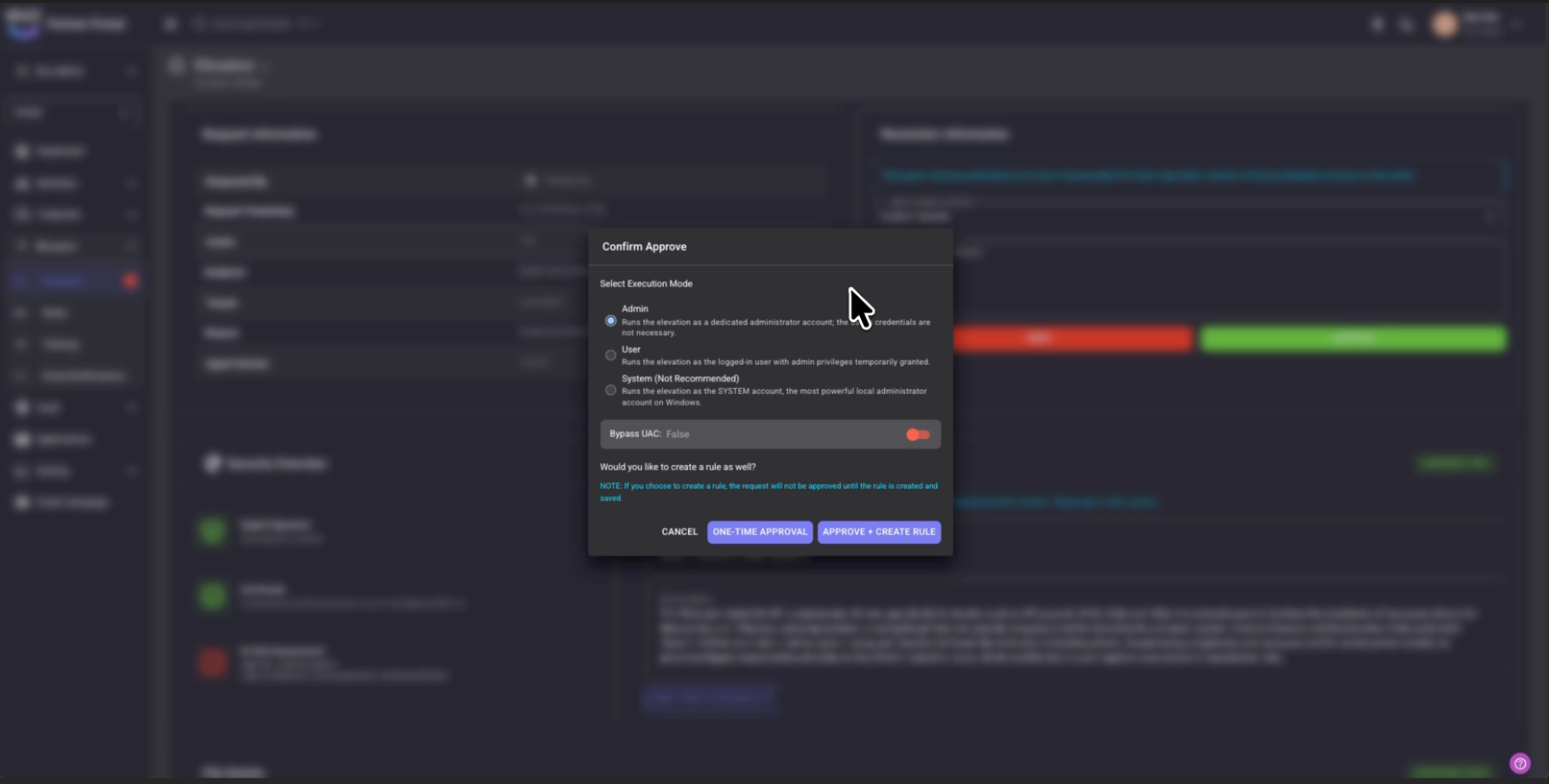
- Control and enforce least privilege for standard users without slowing down support
- Empower end users while removing admin rights through automation and AI
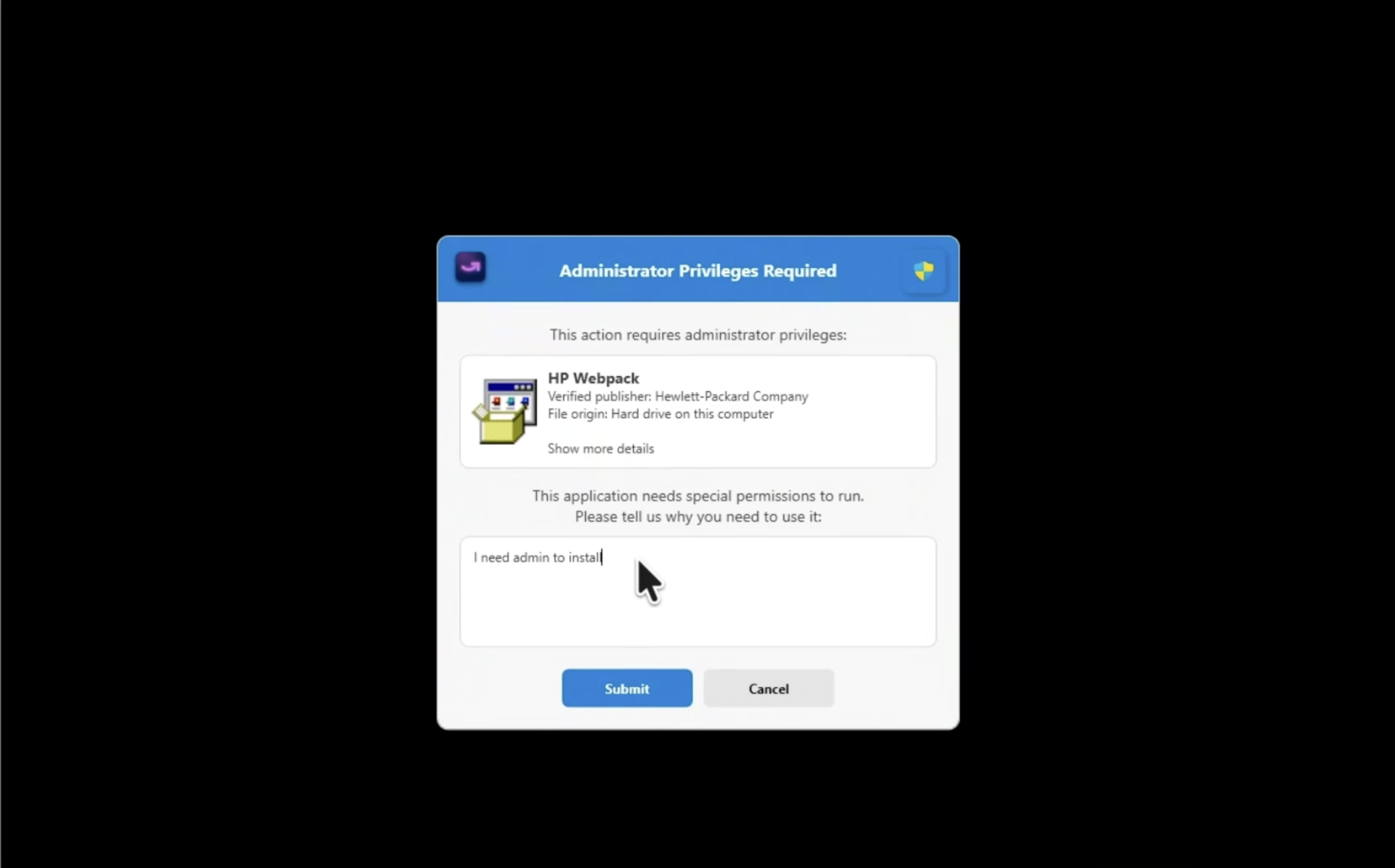
With AI-enhanced, Just-in-Tme (JIT) admin elevation, partners using Evo End User Elevation today benefit from:
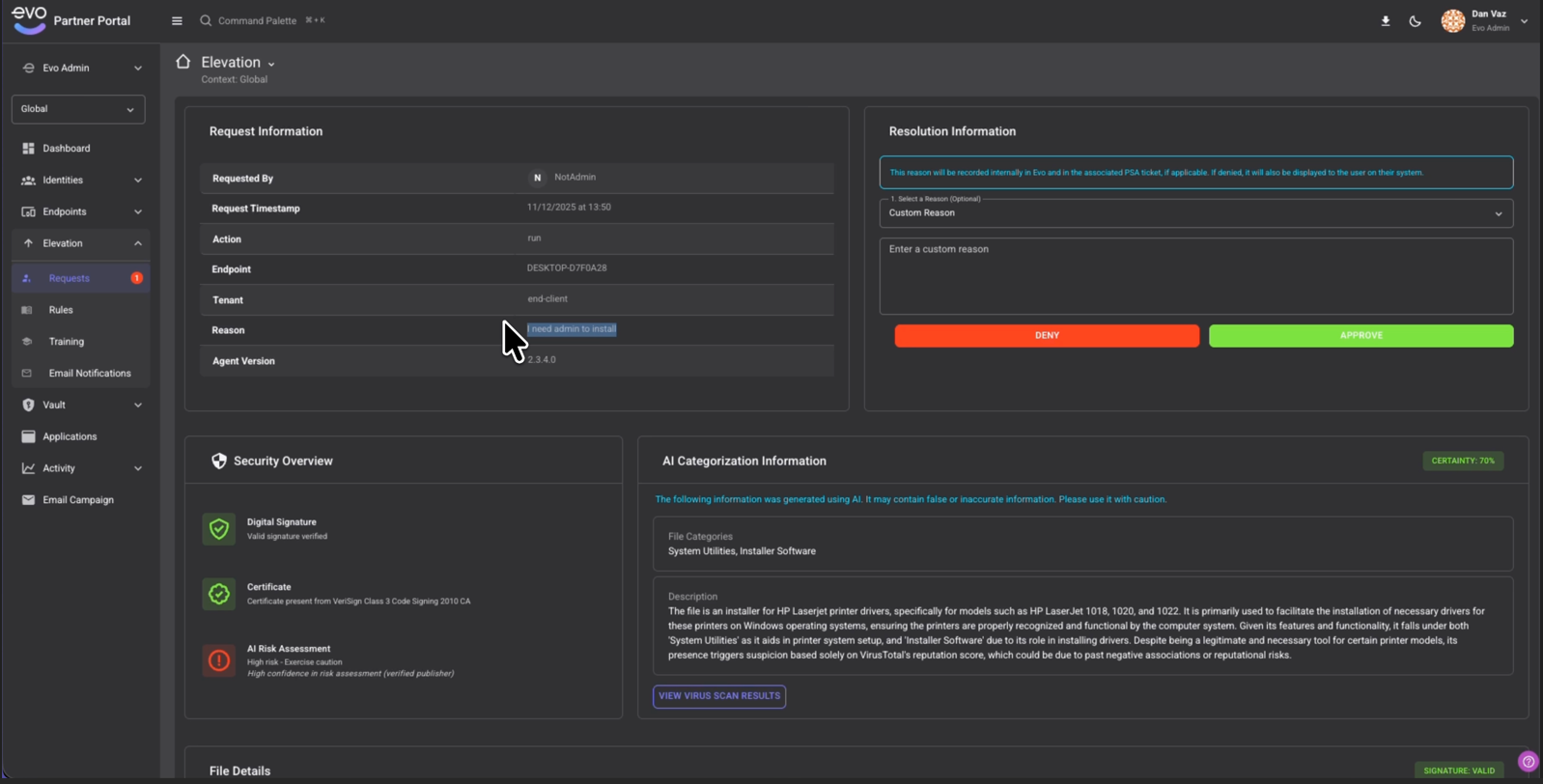
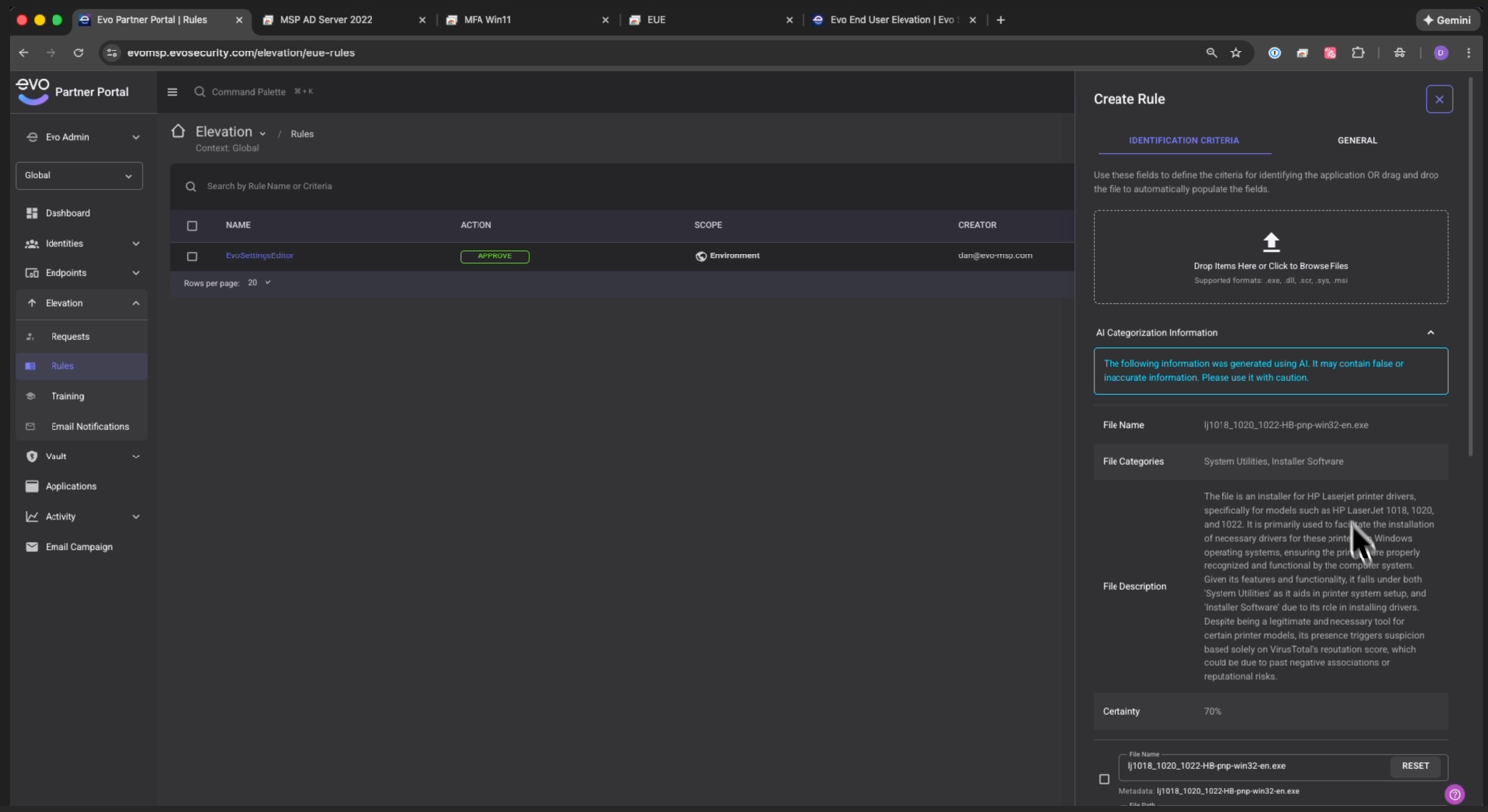
- Deep insights into what a user it trying to install
- Significantly increase approval confidence
- Decreased tickets and technician research
- Reduced ransomware potential
Evo Security helps MSPs reduce support workload, improve customer security, and unlock new recurring revenue – without the complexity of enterprise tools.