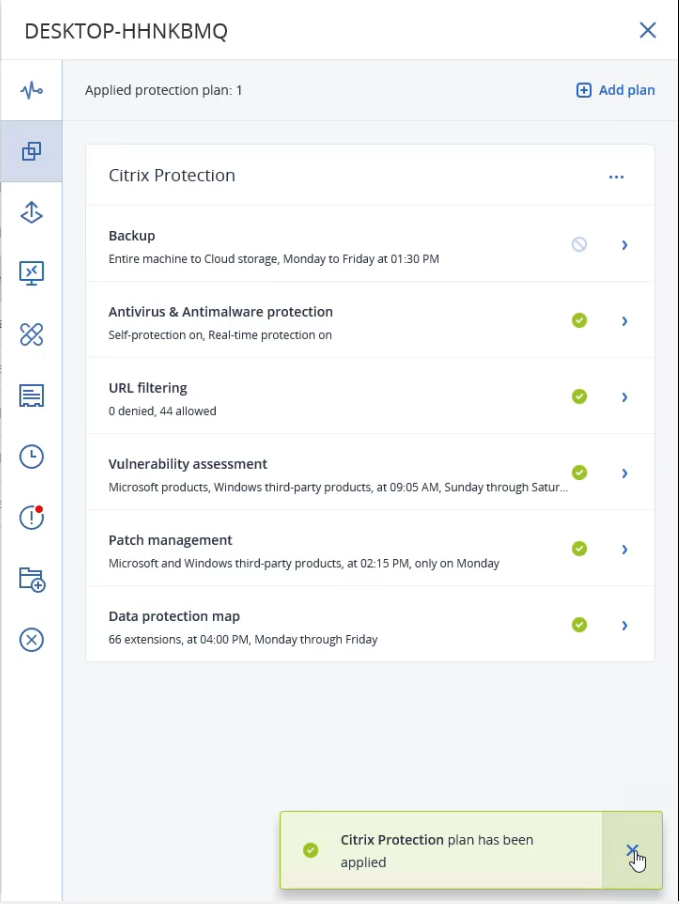
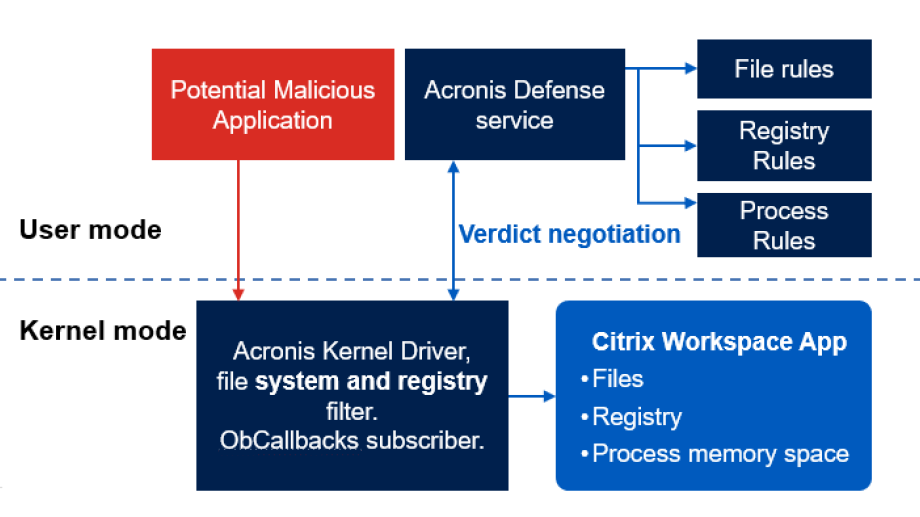
Complete cyber protection for virtual workspaces
The integration of Acronis Cyber Protect Cloud with Citrix Workspace, made possible through the APIs and SDKs of the Acronis Cyber Platform, adds advanced cybersecurity capabilities that enhance Citrix’s existing privacy and security measures.