Impossible Cloud Storage
Features
All data is hot so you always have it at your fingertips in milliseconds without paying extra or sorting files into tiers.
Impossible Cloud works seamlessly with Acronis Cyber Protect and is easy to use and easy to switch with full S3 API compatibility.
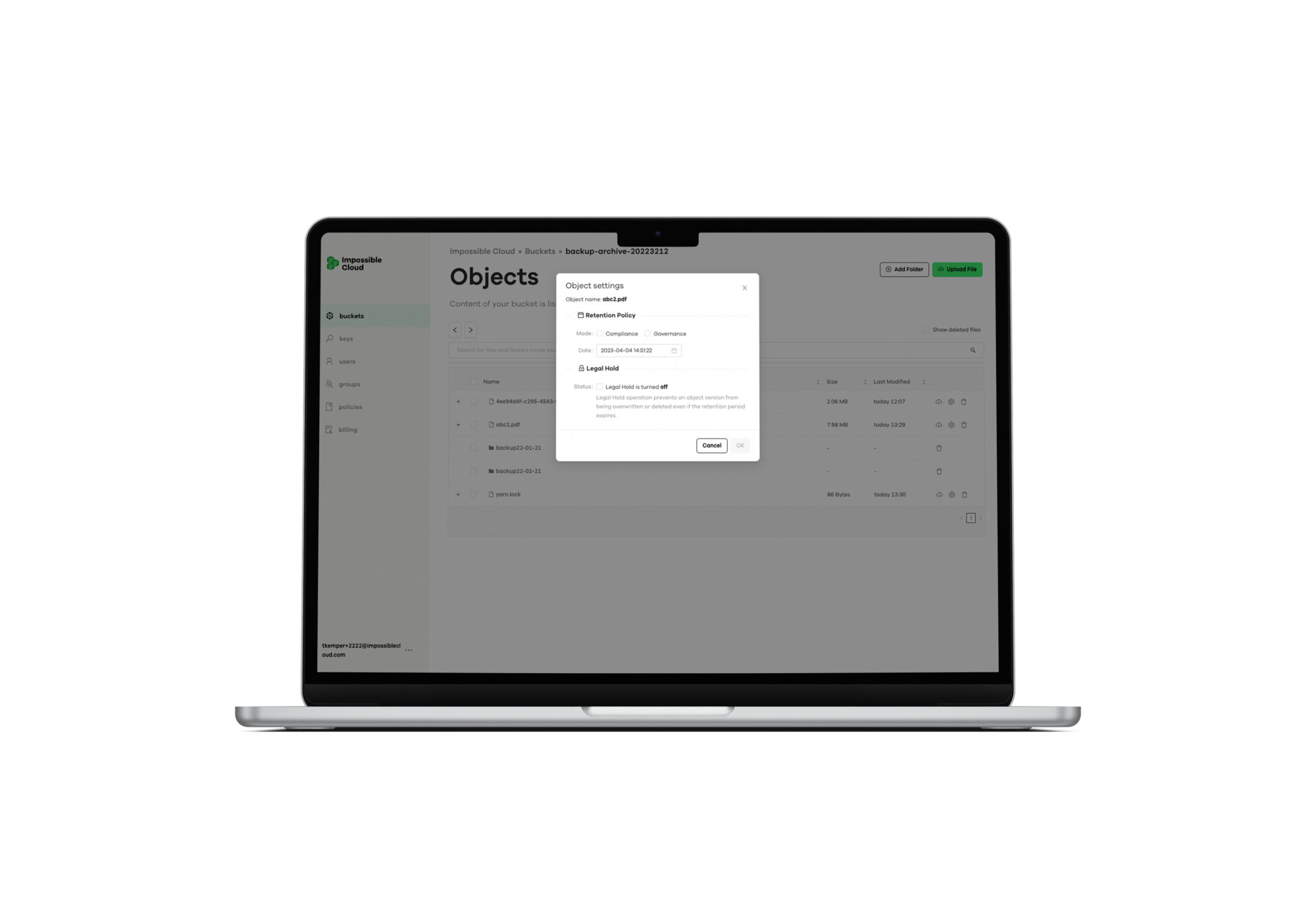
Retain stored files in their original state, rendering them immutable, undeletable, and impervious to ransomware attacks.
Enables you to keep track of all file updates, save a copy of each version, and return to previous versions at any time.
Define multiple users, access keys, sub-users and groups with flexible access rules, enabled entirely via the command line.
Enable adaptive MFA to further secure access to important files and objects, and prevent bad actors from compromising your data.
Every file is encrypted in transit, at rest, and server-side by default, either using the same or a different algorithm.
Protect your data from malicious access on the web such as cross-site scripting (XSS).